In the thirty years I’ve been in the cybersecurity world, I claim that attackers have 3 goals:
- They want to steal/disclose your data
- They want to destroy your data
- They want to use your systems to accomplish steps 1 and 2.
Attack models, e.g., Mitre ATT&CK, etc., describe the techniques used by attackers to accomplish the aforementioned 3 goals.
The main mission of any CISO is not to prevent breaches of their devices or their infrastructure, rather, it’s to protect your organizations’ sensitive data. I’ve said many time in the past that there are no device breach notifications but there are plenty of data breach notification laws. There are many ways to protect data and identity like encryption, monitoring outbound traffic, increasing user awareness, multi-factor authentication. These are important tasks but the most important one is resilience aka recovery. Here are some thoughts.
- We play defense not offense. 95% of companies hire cybersecurity people to defend their company from cyberattacks. They don’t hire them to attack other sites. That’s what the remaining 5% do. However, to play good defense, one must know how to play good offense. In other words, a Blue Team should have strong Red Team skills.
- One must accept the fact that a breach will happen regardless of whatever controls are in place. We will never be able to prevent ransomware attacks. Therefore, we should focus on resilience/recovery. The old defensive strategy of building a “wall” to keep the bad guys out has failed. Monitoring outbound traffic is more important than inbound traffic. While there are many variants of the now popular Zero Trust Network philosophy, there are 3 key assumptions that should govern your defensive strategy:
- The network is hostile.
- Data and identity are the new borders
- Assume the attackers are already inside your net so look for them.
- The key to a successful defensive strategy is resilience not prevention. A sound resilience strategy is key to recovery.
Resilience
I could quote the Webster’s dictionary definition of resilience but let me give you an example.
Ransomware is one of the destructive attacks that has affected a large number of organizations and people recently. It’s been around since 1989 but what made it popular was the introduction of cryptocurrency as the payment mechanism. For example, the Virginia State prescription monitoring database was hit with a ransomware attack in 2009 and the attackers demanded a $10M ransom. The state didn’t pay and restored from backups. There was a disruption of service, some loss of data but the service recovered. Collecting the $10M in small bills requires a bunch of duffel bags and every LEO in the planet would be watching those bags to see who collects them.
This incident convinced me that the best defense against ransomware attacks is not “prevention”, rather, it is “recovery”. A good backup strategy is the best defense in this case. A system gets hit with ransomware, you wipe it, patch it, restore your data from good backups and then move on with your business (figure 2). A good resilience strategy should include these steps:
- Find your sensitive data. If you don’t know where your high risk data is processed or stored, you can’t protect it. Consolidate it into something like a data lake.
- Map where your sensitive data goes within your network borders as well as outside your borders.
- Backup this data lake by taking snapshots, doing old school incremental backups and store the backups offline in a read-only mode. For example, some storage devices allow the creation of a read-only snapshot.
- Test your recovery processes frequently.
The old RFC 1244 “Site Security Handbook” describes two defensive strategies: “Protect and Proceed” and “Pursue and Prosecute”. It set the following conditions for each of these approaches:
Protect and Proceed
- If assets are not well protected.
- If continued penetration could result in great
financial risk.
- If the possibility or willingness to prosecute
is not present.
- If user base is unknown.
- If users are unsophisticated and their work is
vulnerable.
- If the site is vulnerable to lawsuits from users, e.g.,
if their resources are undermined.
Pursue and Prosecute
- If assets and systems are well protected.
- If good backups are available.
- If the risk to the assets is outweighed by the
disruption caused by the present and possibly future
penetrations.
- If this is a concentrated attack occurring with great
frequency and intensity.
- If the site has a natural attraction to intruders, and
consequently, regularly attracts intruders.
- If the site is willing to incur the financial (or other)
risk to assets by allowing the penetrator continue.
- If intruder access can be controlled.
- If the monitoring tools are sufficiently well-developed
to make the pursuit worthwhile.
- If the support staff is sufficiently clever and knowledgeable
about the operating system, related utilities, and systems
to make the pursuit worthwhile.
- If there is willingness on the part of management to
prosecute.
Figure 1. Protect and Proceed vs Pursue and Prosecute
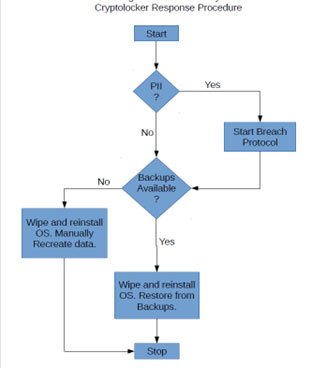
Figure 2. Sample Ransomware Recovery Process
Figure 2 shows a sample ransomware recovery. It is a straightforward process but the 2 critical components are 1) Personally Identifiable Information (PII) search/location 2) consistent and effective backup processes. Once the CISO determines a data breach has potentially happened, they invoke the Data Breach Protocol for their organization. This isn’t a step one takes lightly.
Your ransomware recovery process may include a step listed in RFC 1244 – “Attempts will be made to actively interfere with the intruder’s processes, prevent further access and begin immediate damage assessment and recovery.”
This is an example of resilience. Andy Greenberg’s book “Sandworm” has a chapter dedicated to resilience. Dan Geer’s essay “A Rubicon” is another example of the importance of resilience. Creating an “parallel” network universe addresses interdependency issues and allows for a quick recovery.
We should certainly spend funds on detection tools but the bulk of present-day defenses should be focused on how we recover from an attack. Resilience processes such as backups, monitoring and disrupting outbound traffic to questionable sites are examples of a good resilience strategy.
You’re going to get breached at some point in time. How fast you recover can limit the damage done to your business processes.
References
https://assets.documentcloud.org/documents/4366740/Geer-Webready-Updated.pdf
https://tools.ietf.org/html/rfc1244
https://security.vt.edu/

















