Building control systems (i.e., operational technology or OT) have cybersecurity requirements that cannot be met using the standards available for IT. These IT standards were designed to protect data and data systems. The National Institute of Standards & Technology (NIST) is a preeminent standard for companies developing IT policies and processes. However, even NIST acknowledged the importance of identifying risk in OT devices. Its 2019 publication states that OT/IoT devices identify three high-level considerations that may affect the management of cybersecurity and privacy risks for IoT devices as compared to conventional IT devices:
- Many IoT devices interact with the physical world in ways conventional IT devices usually do not.
- Many IoT devices cannot be accessed, managed, or monitored in the same ways conventional IT devices can.
- The availability, efficiency, and effectiveness of cybersecurity and privacy capabilities are often different for IoT devices than conventional IT devices.
Another noted authority, Gartner, also acknowledged that cybersecurity strategies for OT/IoT require tools, methodologies, and guidelines that are not available in the IT realm.
The net-net is that building control systems need different standards to address their unique vulnerabilities and risks. As a result, the non-profit organization Building Cyber Security(BCS) has created the first comprehensive set of building control system standards.
WHAT IS BCS?
BCS is a private sector non-profit organization of asset stakeholders, technology companies, industry associations, and insurers developing and administering a proactive & holistic framework/certification process with market-based options to improve the cyber-physical security and safety of property and citizens in an increasingly connected world. BCS focused on promoting the adoption of technology, processes, and training to reduce cyber risk.
The Framework Team
BCS formed a working group of experts from the standards community, IT practitioners, and practitioners in the building control space. These individuals represented organizations such as NIST, the International Society of Automation (ISA),the National Electrical Manufacturers Association (NEMA), Center for Internet Security (CIS), and the National Security Agency (NSA).As the building control system industry representative, I was fortunate enough to join this group, affectionately known as the “Breakfast Club,” since our meetings were at 7 AM sharp. We began meeting in August of 2021to determine the standards and their framework.
Choosing the Foundation
The Breakfast Club’s goal was to review all the existing IT standards that might apply to OT and then narrow down from there. After careful consideration, we chose two existing standards to develop the BCS framework:
- The International Electrotechnical Commission (ISA/IEC)62443 standard
- CIS Critical Security Controls Implementation Groups (IG) 1, 2, &3
FRAMEWORK STANDARD #1: ISA/IEC 62443
ISA/IEC 62443 is an internationally recognized standard developed for the industrial process sector’s ever-expanding range of domains and industries, such as power and energy supply, distribution, and transport. This standard’s similarity to the systems and devices in building control systems was naturally more conducive to constructing the BCS standards.
ISA/IEC 62443 has four categories:
- General: Covers topics that are common to the entire standard
- Policies and Procedures: Focuses on methods and processes associated with IACS/BCS security
- System: Requirements at the system level
- Component: Detailed requirement for IACS/BCS devices
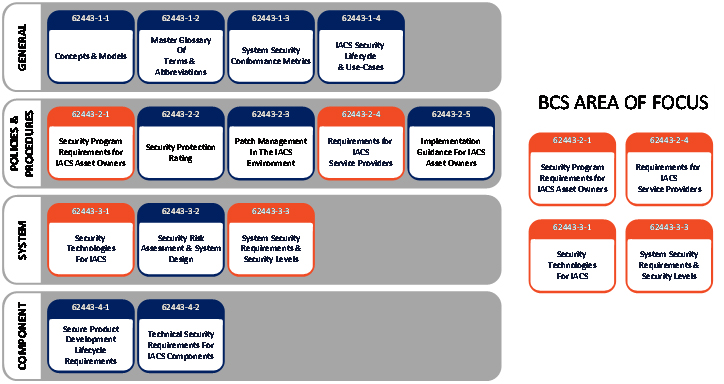
The Breakfast Club worked with one of the ISA/IEC 62443’s authors to determine the controls that best fit the building control system. The main goal was to determine requirements for building owners/mangers, service providers, and manufacturers. In our industry, this area was the most lacking in terms of standards. From the graphic below, you can see the four specific standards that we chose for the framework and how it impacts the roles and responsibilities of each group.
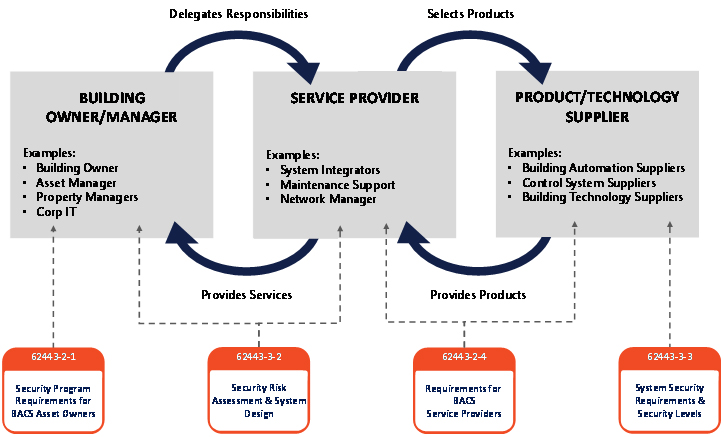
The Breakfast Club also defined Building Functional Areas and added these to the standard for consistent naming and identification. Lack of clarity in naming conventions is a problem across the industry.
| FUNCTIONAL AREA | NAMING CONVENTION |
| A/V and Digital Signage | • Room Management |
| Voice Communication Systems | • Standard • Emergency |
| Utility Systems | • Gas • Water, Boilers, Filtration • Electric (Including Backup Generators, UPS, Solar, Wind) |
| IT Systems | • Data Storage • Financial • Owner Network • Property Management • Tenant Network |
| HVAC Systems | • Ventilation • Chillers • Air Handling • Purification • Air Quality • Health |
| Fire systems | • Fire Detection Systems (alarms) • Fire Protection Systems (sprinklers) |
| People Transport Systems | • Elevators • Escalators • Moving Walkways |
| Physical Access Systems | • Physical Security Control • Video Surveillance • People Count |
| Lighting Systems | • Standard Lighting And Shades • Emergency Lighting |
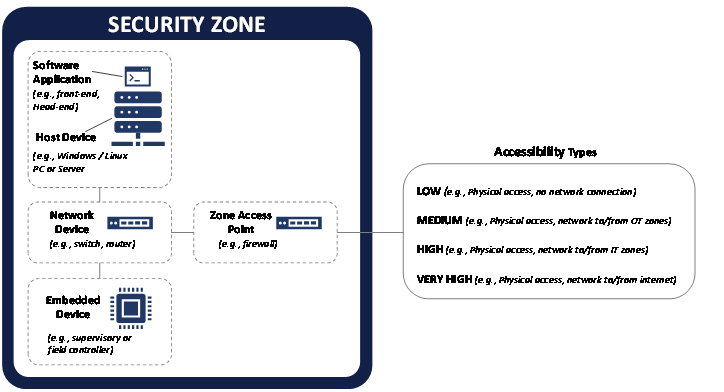
The next task was to define system security requirements. ISA/IEC 62443 uses Security Zones to determine how systems should be grouped. Security Zones are defined as a set of assets with common security requirements. It is crucial to set up Security Zones to separate systems to minimize overall risk and create containment areas if malware/threats have compromised a system.
The image below shows what a typical system Security Zone should look like. It contains a front-end server with the application installed, an embedded device (e.g., supervisory or field controller, and a network device that connects them. The Zone Access Point can be direct physical access only or a remote connection using a firewall. These are defined in the Accessibility Types shown below.
Once a system is in a Security Zone, each is defined as either performing an Essential Function or not. Essential Functions are required to maintain health, safety, environment, and availability of the equipment under control. However, security measures must not adversely affect Essential Functions of a high availability BACS unless supported by a risk assessment.
Typical Essential Functions could be, but aren’t limited to:
- Protection (safety)
- Control
- View/manipulation of the equipment under control
- Physical security
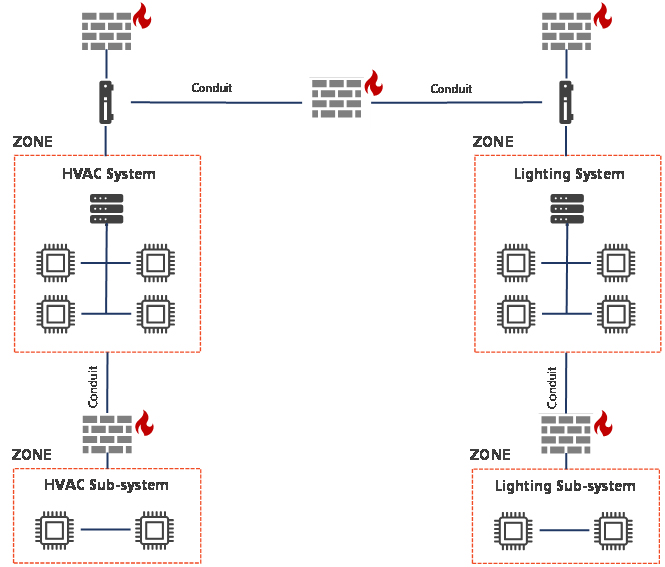
After identifying Security Zones, the systems must be set up to be securely accessed, monitored, and all the assets managed. ISA/IEC 62443 has created a methodology that enables building control systems to comply. This methodology is known as Zones and Conduits. The concept of Zones and Conduits was introduced by the ISA99 committee of the ISA/IEC 62443 series of standards and adopted by BCS to segment and isolate the various sub-systems in a control system.
A Conduit consists of the grouping of cyber assets dedicated exclusively to communications, and which share the same cybersecurity requirements. A Zone is defined as a grouping of logical or physical assets that share common security requirements based on factors such as criticality and consequence. Equipment in a zone has a security level capability. If that capability level is not equal to or higher than the required level, extra security measures must be taken, such as implementing additional technology or policies. The graphic below shows building systems for HVAC and lighting.
FRAMEWORK STANDARD #2: CIS CRITICAL SECURITY CONTROLS IG 1, 2, & 3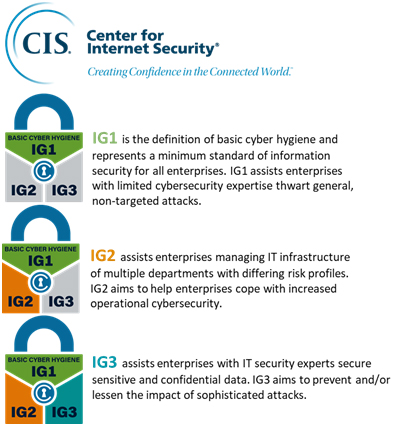
ISA 62443 covered most cybersecurity needs of building control systems, but some components are strictly IT.CIS IGs were included to ensure a full cybersecurity standard. These IGs are based on NIST but have been simplified and categorized to make implementation more digestible for the building controls community. CIS calls the controls inside the IGs Cyber Defense Safeguards. They are broken up into “crawl, walk, run” phases to allow faster adoption and roadmap to maturity.
The image on the right shows the IG levels. IG1 is considered the “crawl” phase. The number of controls necessary to satisfy this requirement is the lowest of the three. IG2 is regarded as the “walk” phase and requires more controls to be met than IG1. IG3 is the “run” phase, which requires that all controls are met.
The second graphic below shows the 18 areas of controls and the number of controls for each phase that must be met. For example, the first image shows Control 01 is Inventory and Control of Enterprise Assets. There are a total of five Safeguards associated with this control. The colored tags indicate the IG and the number of controls required to meet the IG.

- IG1 requires that two of the five controls must be met
- IG2 requires that four of the five controls must be met
- IG3 requires that all five controls must be met
WHAT’S NEXT?
The framework is complete and currently undergoing a review by leaders from manufacturers, insurance, building owners, vendors, and other standards organizations (e.g., NIST). The framework is expected to be released by the third quarter of this year. This means that a building can be assessed and certified, making its building systems safer. This could also impact cyber insurance rates by reducing premiums.
If you would like to learn more, please feel free to contact me (fred.gordy@intelligentbuildings.com) or visit buildingcybersecurity.org.

















