“Many nations have developed privacy protection laws and regulations to guard against unfettered government and private use of personal information. While these protections are important first steps in protecting privacy, existing laws and their conceptual foundations have become outdated because of changes in technology”.
(Professor Kevin Laudon, Markets and Privacy, pp. 92)
One might be forgiven for thinking that Professor Laudon’s assertions were written recently – however they were written twenty five years ago in 1996. Today, data protection laws and privacy regulations continue to be the primary mechanism used by governments to protect personal data. However mandatory breach disclosure – a core element of these regulations – is predicated on detecting/prosecuting a violation after it has occurred, and the damage is done. Privacy regulations are also often reactive and lagging the pace of technology. For instance, the General Data Protection Regulation was in discussion for four years before it was approved in 2016, and then only came into force two years later.[1]In this way, regulation has struggled to keep pace with advances in technology(such as cloud, mobile, social media, and data analytics)or the increasing amount of digital transactions processed/data collected.Thus data breaches continue to rise in frequency and magnitude. In fact over the last 15 years, data breaches in the US, have increased from 57 data breaches in 2005, to 1001 data breaches in 2020[2]. The costs associated with data breaches have also risen – 12% over the past five years – with the average direct financial cost of a data breach in the US in 2020 reported to be between $3.6m and $7.13m[3].
We therefore need to consider revising our corporate approach to privacy – beyond compliance – to include other pillars of privacy that are equally important (e.g., privacy as a human right, an ethical and social concern, and a political issue). Shifting from compliance to include these other pillars of privacy moves the conversation beyond “doing privacy rights” toward “doing privacy right.” This more holistic approach to privacy recognizes that useful or profitable does not equal sustainable, and emphasizes responsibility over compliance. Bart Willemsen, Vice President at Gartner, highlights how building privacy programs that proactively address privacy in this way rather than simply respond to regulation, increase consumer trust[4]. Thus it is likely that ‘doing privacy right’ may present a more effective approach to privacy, associated with more positive corporate and consumer outcomes.
DOING PRIVACY RIGHT
Privacy by Align (PbA). is an approach to privacy, conceptualised by the author to help organizations address the multiple pillars of privacy – not just the regulatory compliance pillars. The PbA approach urges organizations to address the legal/regulatory and incident management pillars as a baseline,and the discretionary pillars as they apply to the organization. The pillars of PbA are summarized in Figure 1.
Figure 1—The Six Pillars Of PbA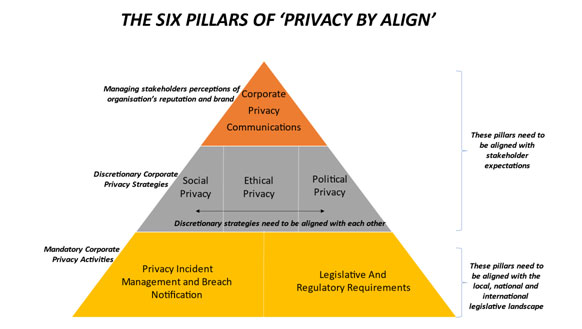
The Six Pillars of Privacy
Mandatory: The Incident Management and Breach Notification pillar, relates to the reporting of incidents to supervisory authorities/regulatory bodies/stakeholders, remediating privacy incident damage, managing possible lawsuits, financial penalties or increased oversight/audits that result.The Legislative and Regulatory pillar relates to consumer, privacy and cybersecurity legislation.
Discretionary: The Social pillar relates to privacy as a corporate social responsibility (CSR) e.g. privacy advocacy, developing open privacy standards, and responding to the privacy expectations of multiple stakeholders (including employees, suppliers, consumers and surrounding communities etc). The process of reaching out to stakeholders to determine what matters most to them is called a ‘materiality assessment’. The Global Reporting Initiative (GRI) provides a useful set of tools for conducting a materiality assessment. The Ethical pillar concerns the way technology is shaping political, social, environmental and moral existence. Alessandro Mantelero’s work combining the Human Rights, Social and Ethical Impact Assessment (HRSEIA) with the Privacy Impact Assessment (PIA), can be a useful starting point to address ethical privacy[5]. The UK Data Ethics Framework[6] and the Omidyar Network’s Ethical OS[7]also provide useful tools for addressing this privacy risk.The Political pillar represents organizational activities such as lobbying for (or against)privacy issues such as national surveillance, freedom of speech, voting, democracy and privacy regulation. Organizations invest millions lobbying governments to favorably shape privacy legislation e.g. privacy was the most frequently used word in the lobbying submissions and was in the top-5 lobby interests of all Big Tech organizations as illustrated in Figure 2.[i]
Figure 2—Big Tech Lobbying Between 2005 and 2018
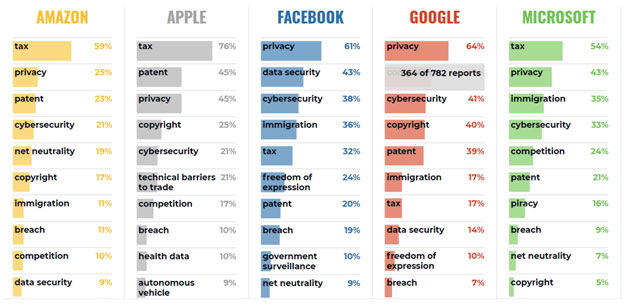 Source: VpnMentor, 2018https://www.vpnmentor.com/research/us-lobby-report/
Source: VpnMentor, 2018https://www.vpnmentor.com/research/us-lobby-report/
Managing Stakeholder Perceptions: The Communications pillar relates to how an organization publishes its privacy values and activities e.g. privacy policies, transparency reports, privacy statements, CSR reports, lobbying databases
Aligning the Pillars of Privacy
The first alignment process consists of aligning activities across privacy pillars (i.e., “to walk the talk”). For instance, organizations that undertake collaborations with privacy advocacy groups (reflecting the social privacy pillar) should ensure that their lobbying submissions (reflecting the political privacy pillar)are aligned. By way of example, in their CSR report, Cisco states that it is leading the development of the EU Cloud Code of Conduct while also lobbying for more comprehensive privacy laws that respect privacy as a fundamental human right.[8]In this way, Cisco’s pillars of social and political privacy are aligned. Misalignment of these pillars can result in reduced stakeholder trust, increased concern for privacy and negative reputational effects.The second alignment process consists of aligning the privacy activities in the pillars with stakeholder expectations toward privacy. Again, using Cisco’s most recent materiality assessment[9]: “data security and privacy” are reported to be of significant importance to Cisco stakeholders and to the organization. In this way, Cisco’s privacy pillars are aligned with stakeholder expectations and will likely result in positive corporate outcomes such as increased consumer trust and reputation.
Conclusion
Organisations need to view privacy with a broader lens that extends beyond just privacy rights – a lens and recognizes the ethical, social and political pillars of privacy. Organizations also need to determine the privacy expectations of the wider stakeholder community. The PbA framework enables organizations to more holistically address privacy by advocating for the alignment of the pillars in order to engender increased consumer trust, reduced concern for privacy and enhanced corporate reputation.
BIO
Valerie Lyons is both Chief Operations Officer, and Senior Privacy Consultant, at BH Consulting, a niche privacy and cybersecurity consulting firm based in Ireland. She previously was the CISO for KBC Bank Ireland for almost 15 years. She has just completed the manuscript for a PhD in Information Privacy. She also teaches a masters program in Dublin City University’s Business School in Privacy, Risk and Ethics. She has contributed to several books, including more recently The CISO Compass and Data Privacy and Trust in Cloud Computing. She is a frequent speaker at International Privacy and Cybersecurity international conferences such as CPDP Brussels, the International Conference or Information Systems, ISACA Eurocacs, ISACA Privacy Summit, and COSAC, and has keynoted at several of their events.
“Doing privacy right” is the focus of Valerie’s PhD research – which is an empirical exploration of how privacy activities in the nonmarket environment can influence both positive and negative outcomes for the consumer and the corporation.
[1] International Network of Privacy Law Professionals (https://inplp.custom/latest-news/article/a-brief-history-of-data-protection-how-did-it-all-start/.)
[2] 2020 Data Breach Report from the Identity Theft Resource Centre (https://notified.idtheftcenter.org/s/2020-data-breach-report)
[3]IBM and Ponemon Institute : Cost Of a Data Breach Report (https://www.ibm.com/security/data-breach)
[4] Gartner predictions for the future of privacy 2020 (https://www.gartner.com/smarterwithgartner/gartner-predicts-for-the-future-of-privacy-2020)
[5]Mantelero, A (2021). An evidence-based methodology for human rights impact assessment (HRIA) in the development of AI data-intensive systems, Computer Law & Security Review, Volume 41, 105561
[6]UK Government Digital Service, Data Ethics Framework (https://www.gov.uk/government/publications/data-ethics-frameworkttps://www.gov.uk/government/publications/data-ethics-framewor https://www.gov.uk/government/publications/data-ethics-framework)
[7] The Ethical OS (https://ethicalos.org/)
[8]Storer, K.; “Cisco Calls for Privacy to be Considered a Fundamental Human Right”
[9] Cisco Materiality Assessment (https://www.cisco.com/c/m/en_us/about/csr/esg-hub/governance/materiality.html)

















